Crack the hash
[TASK 1] Level 1
48bb6e862e54f2a795ffc4e541caed4d -> easy
Paste this hash on the crackstation website and you will get the result.
CBFDAC6008F9CAB4083784CBD1874F76618D2A97 -> password123
1C8BFE8F801D79745C4631D09FFF36C82AA37FC4CCE4FC946683D7B336B63032 -> letmein
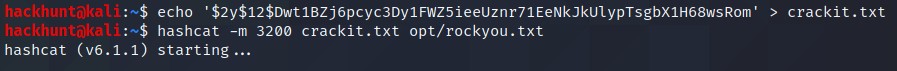
$2y$12$Dwt1BZj6pcyc3Dy1FWZ5ieeUznr71EeNkJkUlypTsgbX1H68wsRom ->
Using Hash Analyzer, it says bcrypt. So we will use hashcat.
hachcat -m 3200 <has> <wordlist>
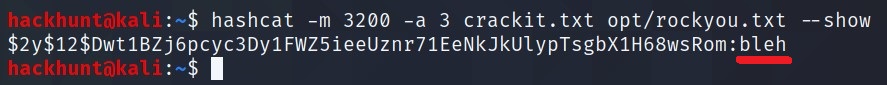
279412f945939ba78ce0758d3fd83daa -> Eternity22
[TASK 2] Level 2
F09EDCB1FCEFC6DFB23DC3505A882655FF77375ED8AA2D1C13F640FCCC2D0C85 -> paule
Crack Station or
hashcat -m 1400 <hash> <wordlist>
1DFECA0C002AE40B8619ECF94819CC1B -> n63umy8lkf4i
Crack Station or
hashcat -m 1000 <hash> <wordlist>
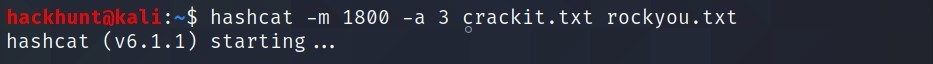
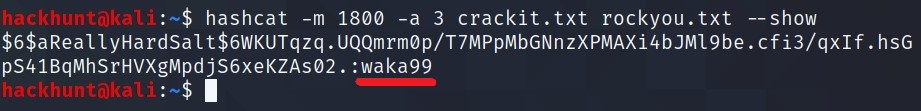
$6$aReallyHardSalt$6WKUTqzq.UQQmrm0p/T7MPpMbGNnzXPMAXi4bJMl9be.cfi3/qxIf.hsGpS41BqMhSrHVXgMpdjS6xeKZAs02 -> waka99
Hash is sha256crypt. CMD ->
hashcat -m 1800 <hash> <wordlist>
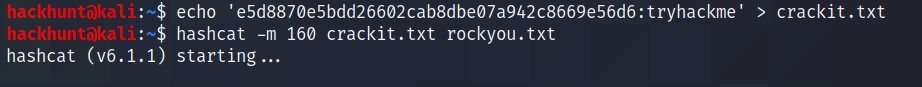
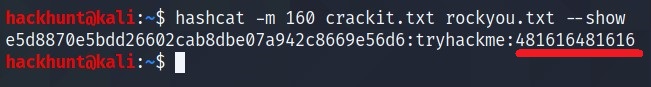
e5d8870e5bdd26602cab8dbe07a942c8669e56d6 -> 481616481616
Hash is SHA1 (with salt). We can use
160mode in hashcat. Save the file ashex:salt. Hashcat CMD ->hascat -m 160 <hash> <wordlist>
Alternatively, John The Ripper can be used. To specify the type use --format flag.
To know which kind of HASH, pre-installed tool like hash-identifier or hashid can be used expect from the online version like Hex Analyzer.